Binary Exploitation [pwnable.kr] - (Level 4) flag
#Challenge Description
| Name | flag |
| Points | 7 |
| Solves | 10695 times |
| Category | Exploitation |
| Description | Papa brought me a packed present! let’s open it. This is reversing task. all you need is binary |

The challenge binary can be downloaded from this link.
From the description seems like it is a reverse engineering task. Let’s download the binary and load it up in ghidra.
#What is a Packer?
Packers are the program binary that compresses the original program and create a new program binary called packed binary, this new binary has the code to decompress the original program and run it. When you execute the packed binary it first executes the decompression code that unpacks the original program in the process memory and then transfers the control to the original program for execution. Packer program can pack and unpack the program without source code of the original program.
Compression is not the only thing that packers do, they might even introduce a code that checks if the program is been debugged or if the program is executed in a virtual machine. It might even encrypt the original program and decrypt it only certain conditions are met. The general idea is there is a code that runs before the original program which controls its faith of execution.
Why all this hustle? you might ask. There are many reasons why this kind of product exist in the market:
- A malicious program which when to evade antivirus static signature match. Since the packed program hash is different from the original program.
- To reduces the size of the original program so that it can store their program in a stringent environment.
- When someone protects their code from been reverse engineered.
- A malicious program which doesn’t want to run in an environment where they are monitored like a debug environment or in a virtual machine.
I can go on and on about this topic, but the crux of the matter is of challenge binary is hidden behind a packer program.
#Hint
There are many packers in the market on one of the most popular packers is UPX, it supports many platforms like Windows, Linux, etc and also support different architecture exotic architecture like x86, ARM, SPARC, PowerPC, etc. You can execute the simple command to compress/decompress the binary. To decompress the binary execute upx -d
This cover the first clue. Once you execute the unpacked program you will be presented with the second clue to solve the challenge. Which is I will malloc() and strcpy the flag there. take it.. Revere engineer the unpacked binary and check the parameters of the function mentioned in the hint you will have the solution.
#Solution
Once you load the binary in ghidra and go to the main function you will see below disassembly.
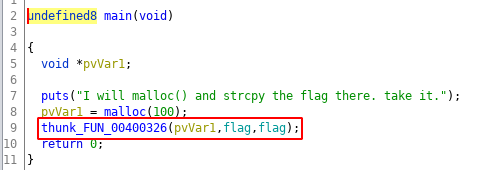
As the hint says there is a malloc followed by strcpy, but I can’t see any strcpy? exactly that was my first thought but then there is flag variable been used on line 9. Let see what that variable has?
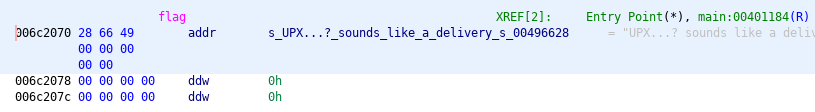
The variable seems like a reference to a string, let’s click on the reference and see what the string value is.
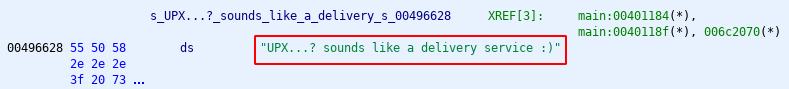
Looks like a flag to me. Submit the flag and you have completed the challenge.
If you inspect the rest of the binary or follow thru_FUN in the above main function then you would have wasted a lot of the time reversing needlessly, that what I did initially when solving the challenge. Maybe it was a decoy for the over smarts folks.
#Conclusion
I would say this is the most simple challenge if you follow the hints. The new tool which was introduced was a packer and we looked very briefly at it used that knowledge to unpack the challenge binary and then reverse-engineered the binary to get the flag.